Many businesses that start developing software products are primarily focusing on getting the product to market asap. When the same business grows, the priority and focus change over time as well. But at the end of the day, the same business that handles and interacts with customer data either ignores, forgets, or de-prioritizes the importance of data privacy. And in some cases very sensitive data like personal financial information, health information, etc. It does not matter if your business is little or big. If the business does not take this into consideration, this could lead to catastrophic consequences for the business and the customers.
For instance, Netcompany (one of the biggest software developers in Scandinavia) has recently accomplished a Dkk 200 million project for the government to handle citizen electronic posts. The product called mit.dk was launched and on the same launch day, users were able to see other citizens’ personal posts that contains highly sensitive data. Reference to Article in Danish. Btw this business was not small, it is started by a bigger company and a good repetition and good budget. So this could happen for any business size.
So the question comes, what can a business do to have a process and a strategy for Data Privacy? What should the business do in case of data breaches and leaks? and so on.
In this article, I will take a couple of examples of how to handle sensitive data. And later recommend a book that can enlighten you covering some of these questions.
Let’s now take an example, let’s say we have the following JSON payload that contains personal information.
We will take 2 examples here of how to handle this data from internal and external stakeholders.
{
"request": {
"timeStamp": "2022-01-10T05:06:44.160Z",
"transactionId": "1232a25a-f143-45d2-a614-b59b9b0ea5dc",
"client": {
"clientName": "John Doe",
"clientSsn": "P3333553324",
"gender": "Man",
"birthDate": "05/03/1982"
}
},
"response": {
"loanAmount": "ddk100000",
"approval": "failed"
}
}Data Encryption for external stakeholders
It is true that many firms use secure communication like (secure email or SSL) between sender and receiver. Let’s say your software collects sensitive financial data for a client that applies for a loan, and for some reason, the client application failed and needs to be investigated by the bank client support team. The bank client support team might not be in the same location as the technical support and software team.
So the support team wants to send this sensitive information to the external client support team at the external location?
In this case, the bank should have a self-generated RSA certificate with private and public keys using a library like CryptoNet or other libraries. The technical support team has the public key to encrypt the content and send the encrypted content to the client support team so they can decrypt the content using the private key.
This practice is good in case the email system gets hacked, so the content of the email is not readable, or if 3rd person outside gets hands on the file that contains the data, it will be encrypted.
Data anonymization for internal stakeholders
Let’s say the same data above, need to be analyzed by the business intelligence team, so they can create an overview of the number of applicants, the age, gender, loan amount, and the approval result.
This means when we provide data to the business intelligence team, we could easily anonymize specific fields to comply with GDPR. For example client name, social security number (snn), and birthDate. Regarding the birth date, we can eventually anonymize it by changing the month and day to 01/01 and keeping the year to calculate the age.
Most importantly is that we should not able to reverse engineer the client data. And of course, this needs to be aligned with Data Protection Officer or Compliance attorney.
So this is what our anonymized data looks like.
{
"request": {
"timeStamp": "2022-01-10T05:06:44.160Z",
"transactionId": "1232a25a-f143-45d2-a614-b59b9b0ea5dc",
"client": {
"clientName": "39074cb6-360c-4be4-9b59-4812483e2024",
"clientSsn": "2b3ff6c6-458f-4168-b65b-3902b3db54ef",
"gender": "Man",
"birthDate": "01/01/1982"
}
},
"response": {
"loanAmount": "ddk100000",
"approval": "failed"
}
}Conclusion
With all that said, Data Privacy is a huge and wide area with a lot of attention. It has a lot of details that can not just be covered by a little article like this, and as Software Engineers, we talk often a lot about Data Privacy and how to handle data in general. Therefore I have had a unique opportunity to review a book called Data Privacy by Nishant Bhajaria from Manning publications.
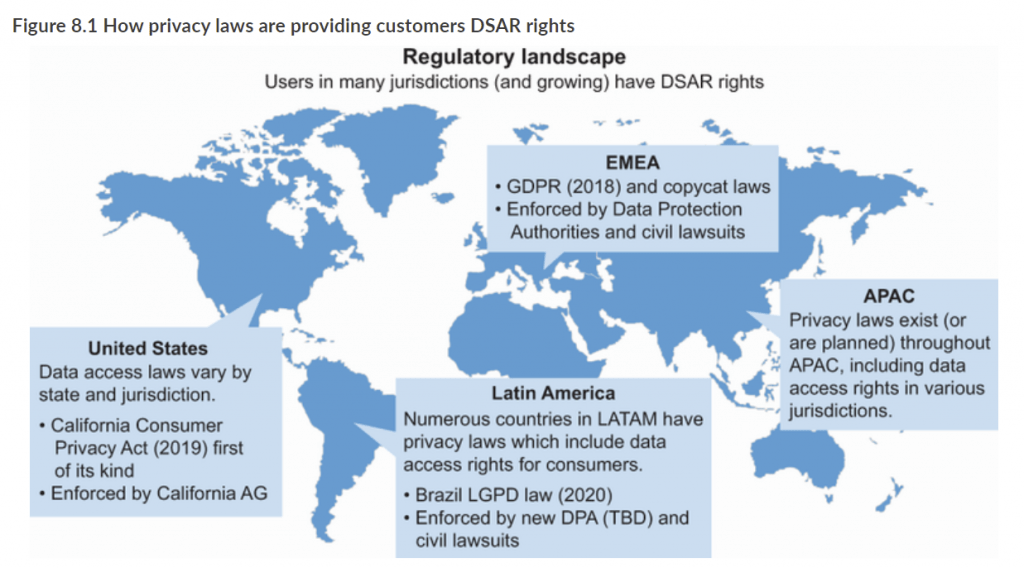
This book contains a lot of useful information, examples, and inspiration that go into detail that I use to solve my Data Privacy issue in my real-world job.
I personally encourage software developers, architects, business owners, product owners, or people who work with data in general to have this book.